|
Telnet is a terminal emulation program for TCP/IP networks such as the Internet. The Telnet program connects your computer to a remote server. You can then enter commands through the Telnet program and they will be executed as if you were entering them directly on the other end. This write-up will explain Telnet in both Mac and Windows.
There are two basic Telnet programs for Macintosh computers, namely, Better Telnet and NCSA Telnet. NCSA Telnet is a freeware developed by the National Center for Supercomputing Applications, which is located in the University of Illinois at Urbana-Champaign.
How to Connect to a Server
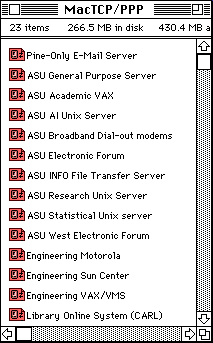
By clicking iconIn a system where configuration is preset, NCSA Telnet is transparent. i.e. you don't need to perform the telnet procedure. Instead, icons for different telnet sessions have already been made as shown in the following:

Simply click open the icon and it will connect to the server. However, sometimes it does not work for three possible reasons:
- The preset icons may not have the server that you want to connect.
- Preset Telnet icons are data files created by NCSA Telnet. Sometimes your Mac may fail to open a file and tell you that "the original application is missing" even though NCSA Telnet is there.
- The Domain Name Services (DNS) server malfunctions. The function of DNS is to translate a host name into internet protocol (IP) number. For example, when NCSA Telnet asks for a connection to general.asu.edu, DNS server will convert the name to 129.219.10.145.
In either one of the above cases, you have to use Open Connection in NCSA Telnet as the following procedure indiciates.
By Open Connection
Open the software NCSA Telnet instead of clicking a preset icon. Then choose Open Connection from File menu.
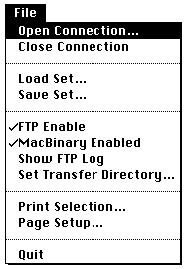
You will see a dialog box as shown in the following. Enter the host name or the IP number in the field Session name (If DNS fails, you must enter the IP number). The default name of the Window session is the host name. You can leave the window session field blank. Then click OK.
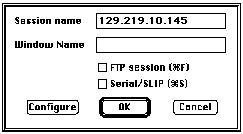
By Open SpecialIf the administrator has set up different servers at the preferences of NCSA Telnet, you can request a preset connection by openning special session. The procedure is to pull open Open Special from File, then pull open a particular server that you wants to login:
How Keys Work
After you connected to the host, you can do full screen edit. NCSA Telnet emulates an VT102 terminal, and therefore your Mac should have a clean interface with most systems. In case of interface problems, in UNIX you can set the terminal type:
% set term=vt100;tset
If the terminal reset is successful, the numeric keypad on your Mac keyboard should match the function keys of the host computer. i.e. clear is F1, \ is F2, = is F3 and so on.
Control-C is one of the universal interruption command in different platforms such as DOS, UNIX, and VAX. In NCSA Telnet you also can interrupt a process by pressing Control-C.
How to Switch Sessions
NCSA Telnet allows you to have multiple connections to a single host or to several different hosts. You switch windows back and forth by choosing a session from the pull down menu Connections.
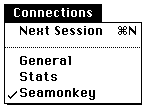
How to Test the Connection
Occasionally, a congestion in the host occurs because there are many clients at the same time. It seems the host is not responding and you doubt whether your terminal is locked up. In this case, you can choose Are You There? from the Network menu.
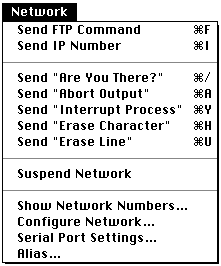
If the problem is a traffic jam rather than a lockup, the host should send you a message to verify that the connection is still up.
Windows has a built-in Telnet program. To run Telnet on a Windows computer, you literally open Run from Start, and then type "telnet [server name or IP number]".
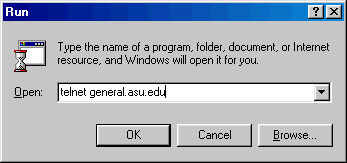
Once you have visited a server, Telnet will automatically bookmark the server address. Next time you can simply type "telnet" in Run, and then choose an address from the Connect menu.
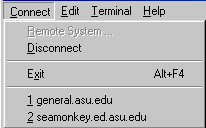
You can also invoke Telnet through a Web browser. To do so, type "telnet:" in the location bar (where you enter URLs) and press Enter. You may ask me why. In some public computer labs, network administrators may hide the Run option and lock the hard drive to protect the system configuration. Without full access to the system, you can still open Telnet via a Web browser.
Please be cautious to potential hackers. In regular Telnet session, IDs and passwords go around the Internet as clear text. It is not difficult for a hacker to capture the data package. To counteract this threat, some organizations use a commercial Telnet program named SSH Secure Shell. The Telnet interface of SSH Secure Shell is the same as that of other Telnet programs except it encrypts transmitted information. F-Secure has Mac, Windows, and UNIX versions.



|
Network Contents
|
|